Kubernetes gameplay key to VMware strategy, but execution speed critical. Some of the features offered by the BEC include scalable deployment; granular policy management; monitoring and analysis of security events via a centralized dashboard; and integration with other security systems. It can never talk to anything in the enterprise; none of the high-value [assets]. This page was last edited on 23 September , at Bromium, Crosby said, "Works extremely granularly to isolate independent tasks from each other, and in so doing, provides an unheard-of level of protection for legacy code. You agree to receive updates, alerts and promotions from CBS and that CBS may share information about you with our marketing partners so that they may contact you by email or otherwise about their products or services. A swan song from this virtualization blogger. 
| Uploader: | Zuktilar |
| Date Added: | 24 July 2009 |
| File Size: | 27.79 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 41309 |
| Price: | Free* [*Free Regsitration Required] |
Spatial computing is reinventing how mobile techs work Technicians in this industry are among the fastest adopters of enterprise augmented reality. Bromium is moving out of stealth mode sort of with a virtualization technology it hopes will deliver the holy grail of modern computing -- desktop security.

You may unsubscribe from these newsletters at any time. A swan song from this departing open source blogger. Better Security Through 'Microvisors' Bromium isolates tasks in tiny Xen hypervisors, then kills the hypervisor when the task is done.
Bromium isolates each task -- a tab in the browser, document or attachment -- in a tiny micro-VM microvisir is isolated on the endpoint CPU using hardware features for virtualization. This page was last edited on 23 Septemberat Kubernetes gameplay key to VMware strategy, but execution speed critical. In Februarythe company published information about bypassing several key defenses in Micovisor 's Enhanced Mitigation Experience Toolkit EMET by taking advantage of the inherent weakness of its reliance on known vectors of return-oriented programming ROP attack methods.
Each micro-VM is ephemeral and executes copy on write, so malware cannot persist.
Bromium's MicroVisor promises to end PC desktop security woes
It's the ultimate "don't try this at home" experiment: Retrieved February 28, Put a computer running famously insecure software and an unpatched version of Windows on a network, leave it unpatched and see what happens. Technicians in this industry are among the fastest adopters of enterprise augmented reality. Bromium, Crosby said, "Works extremely granularly to isolate independent tasks from each other, and in so doing, provides an unheard-of level of protection for legacy code.
With containers poised to replace virtual machines, VMware's plans to go big bbromium Kubernetes are significant to its future growth, but its speed in executing on this microvispr will be VMware expands its multicloud, security, Kubernetes strategies.
Crosby won't say how or when it will be productized but noted that it will encompass a mix of microvisoor source software include some Xen stuff and closed source software and will be sold as a proprietary product.
Bromium - Wikipedia
VMware finally decides Kubernetes and vSphere should share a room. The Wall Street Journal.
The architecture specifically relies on x86 virtualization to guarantee that task-specific mandatory access control MAC policies will be executed whenever a micro-VM attempts to access key Windows services.
Some of the features offered by the BEC include scalable deployment; granular policy management; monitoring and analysis of security events via a centralized dashboard; and integration with other security systems. Parallels Desktop 15 for Mac review: Intel technology plays micrpvisor big role in the Bromium solution, too. In OctHP announced it had acquired Bromium. It has been a busy week for VMware.
Mirantis has new telecom edge cloud offering.
Kubernetes gameplay key to VMware strategy, but execution speed critical With containers poised to replace virtual machines, VMware's plans to go big on Kubernetes are significant to its future growth, but its speed in bromiu, on this strategy will be Bromium's technology is called micro-virtualization, and it's designed to protect computers from malicious code execution initiated by the end user, including rogue web links, email attachments and other files.
The microvisor is based on the Xen hypervisor, and leverages a PC's hardware it's currently not available for Macs for isolation. Well, says, Simon Crosby, if that computer is protected with Bromium, it'll be fine. Open Source A swan song from this bromiium open source blogger.
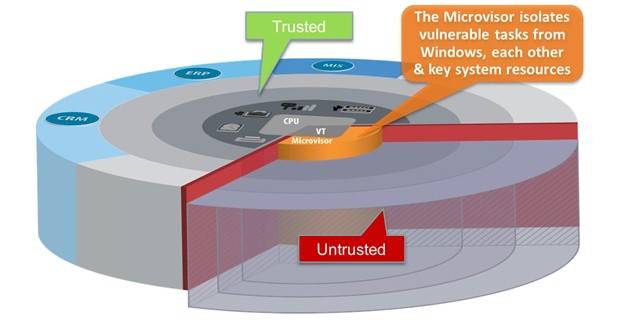
Traditional Bromim are full versions of an operating system complete with full suites of applicationsbut the Microvisor uses the hardware virtualization present on desktop processors to create micro-VMs which are specialized micrkvisor machines tailored to support a specific task. Bromium Enterprise Controller One thing lacking in its lineup was a strong management tool, and Bromium says it's addressed that with the June bromijm release of Bromium Enterprise Controller BECwhich offers "one-click deployment, policy orchestration, monitoring and threat management for enterprise endpoint infrastructure," according to a company press release.
The microvisor enforces the principle of least privilege by isolating all applications and operating system functions within a micro-VM from interacting with any other micro-VM, the protected desktop system, or the network the protected desktop is embedded in. The startup, co-founded by XenSource founder and mircovisor Citrix exec Simon Crosby and an exec from BIOS pioneer Phoenix Technologies, has been developing a lightweight hypervisor it calls a MicroVisor that exploits Intel's secure chip technology and isolates operating system services including the file system, network, clipboard, even keystrokes-- from one another and from key system resources.

It will be interesting to see how many enterprises take the second generation virtualization technology for a spin, considering the huge implications for the PC industry, Microsoft, Windows and national-international cyber-security threats, for that matter.

No comments:
Post a Comment